The Uncrackable MD5 Hash Generator Online
Website services rely heavily on user authentication passwords. It is to help users to generate and choose stronger passwords, a password generator online services are becoming more and more popular as they can generate strong authentic passwords in just a matter of clicks, which are never be hacked or guessed by hackers, who search and view your online history in order to hack your online accounts or personal history.
Password counters or websites estimate the strength of passwords which are provided by users. Online password generators or even MD5 hash generators can help users generate stronger passwords.
This article would help to focuses on the state of the art technique of these passwords and MD5 hash generator on the Internet. Orthogonal to the large amount of work on password measures that we focus on password and MD5 hash characters which can be entered directly on the web. The online working technique of password or MD5 generator depends on the large-scale empirical approach and the study of web password generators. It also relies on the ubiquitous reliance on the third-party code for access passwords.
Generate a Strong MD5 Hash using Your Text Value
- To generate strong MD5 Hash value go to https://www.safepasswordtool.com/md5-generator.php
- Enter the text you want to md5 hash converted.
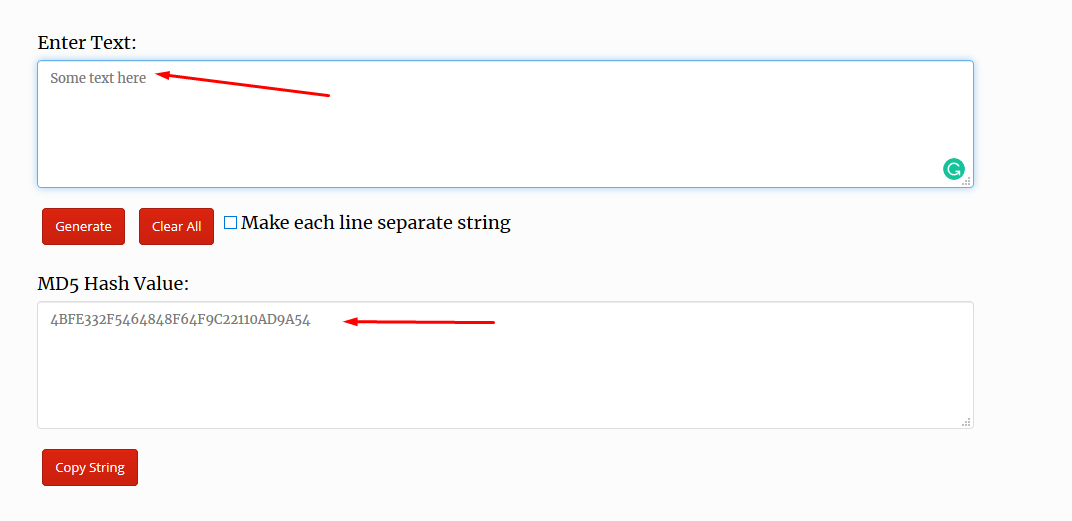
Passwords are often sent over the network, invisible to users and sometimes in plain text. It is important to improve them in the different character from. An online general network framework can enable secure and modular password porting in generation modules. The utility of the framework through a reference implementation is important to review its authenticity.
The Importance and Usage of Passwords and Online MD5 Generators
MD5 Hash is a crpytographic hash that uses a checksum for verifying data such as passwords and cookies. MD5 Hash is a one way encrpytion meaning there is no way to decrpyt it back to its original text value.
The use of passwords on the internet is quite useful and vulnerable too. Although a variety of authentication mechanisms are proposed for password authentication, e.g. the combination of username and password with the access data stored on the server, it is still a common type of authentication that can work on the internet.
The databases of the user’s credentials can often escape after a website is compromised. Password prescribe best conservation practices include storing passwords with hashes and with strong encryption
unidirectional hash algorithm with a specific identification information. For cracking a password, any motivated hacker can try reversing stored hashes with clear password hacking techniques or with special tools like ‘John The Ripper’. To decrypt a password hash, they can create password crackers, hash the candidate passwords and compare them with the original hash. If a match is found, the original password can be restored or at least one password that gives the same hash value.


Cool md generator. been using it for a while now.
I wanted to know how to track my wife’s phone without her knowing and was pleasantly surprised to find [email protected]. It is a great hacker for tracking her phone activities without her ever knowing. I highly recommend it to anyone who needs to keep track of their spouse or loved ones. His spy app user interface is very easy to use and understand. It allows me to view all of my wife’s activities on the target device, location tracking, and other features such as social media account monitoring. This tool has saved me a lot of time and worry in knowing that I can keep tabs on her without her ever knowing. Highly recommend this hacker.
Your method is incredibly impressive. It’s clear that you have a deep understanding of X and are passionate about sharing your knowledge.
I’m blown away by this method, thank you for showing it to us.
Thanks so much for sharing your method! It’s incredibly helpful and effective. Great job!
Your method is incredibly insightful and helpful. It’s made me realize that there’s always room for improvement and growth.
The simplicity and elegance of your method are truly remarkable. I appreciate the effort you’ve put into distilling complex concepts into easy-to-follow steps.
This method has completely changed my perspective on X. I can now approach it with confidence and a clear plan of action.
I Spent several useful hours trying some spywares, but it didn’t work till I finally saw a reference to this Andrew Hacker who did an amazing job. I’ll never have to look for hackers online again. However, You wonder if your wife/husband is something behind your back. You suspect your wife/husband is lying to you. Find out the truth and bring peace to your mind with this HACKERS contact gmail [email protected] and you can text,call him on +15177981808