The Ultimate Guide About Doxing
The Internet, although considered as a useful place by many for everything it helps them do, also attracts a lot of criticism for having a dark, negative side. There have been a whole lot of crimes related only to the Internet, usually termed as “cyber crimes”. In fact, it’s also responsible for many people’s deaths throughout the world, due to the wrong practices followed by many Internet users.
What is doxing?

However, in this article, we will be taking a look at only one particular thing, usually known as doxing, which may or may not be a crime, depending on the intention of the one who does it. Doxing, in simple words, is a process that involves collecting someone’s private information using the Internet. It’s believed to be similar to hacktivism and Internet vigilantism.
Such private information may include one’s name, location, email address, phone numbers, age, and so on. Usually, someone resorting to doxing for collecting information about you may use the search engines, social media websites, and sometimes, many other services.
Methods of Doxing Somone
First off, this might not be the best doxing tutorial you will read. This is a startup I guess. Let us now go through some of the common types of doxing in detail.
-
Using search engines such as Google
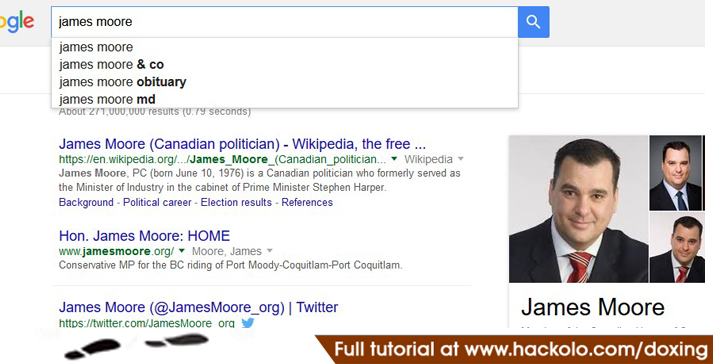
Google has always been the favorites search engine of most people for almost everything they need done, and doxing is no exception. Google is arguably the biggest search engine out there and it seems to be indexing just about everything, including the people’s private details.
However, someone may not necessarily find your private details through Google just because they want to. In order for your private details to get indexed, they need to get shared at least once on the Internet. If you haven’t shared any of your details ever, and are pretty sure that even no one else did, you should be safe enough from doxing.
But usually, those new to the Internet and online activities don’t really understand these things, and would put their private details just about anywhere. This makes it more than easy for doxing your private information. All someone would have to do is do a simple Google search, and they would find the details they are looking for in the description of the first few results.
Example for using Google for Doxing:
- Searching the name/nickname/username or anything you know related to that someone and collecting results which you seem to be closely related and search the results for more information collected.
- Search and analyze for links or websites closely-related to the someone you are doxing.
-
Social media

Using the major social media websites like facebook, twitter, instagram and youtube it seems to be another very common and easy way of doxing someone’s private information. Many users, especially the new ones, post almost all the details the social media websites ask for, but forget or don’t know anything about changing their privacy settings in order to safeguard themselves from potential doxing attempts.
Getting doxed through social media websites can lead to more problems for you, as it may end up giving even more information, including your private pictures, interests, workplace details, details of your friends, and so on.
In other words, social media sites may actually work as a goldmine of information for someone who is looking to dox you. As the privacy settings aren’t strong enough by default, you may be giving away your private information easily to anyone who looks for it through your profile.
Sites such as Facebook and LinkedIn are believed to be some of the most common social media networks that can be easily be used for doxing. It’s due to the fact that they require one to share quite a lot of information, while the privacy settings are usually quite weak by default.
-
Reverse cell phone lookup
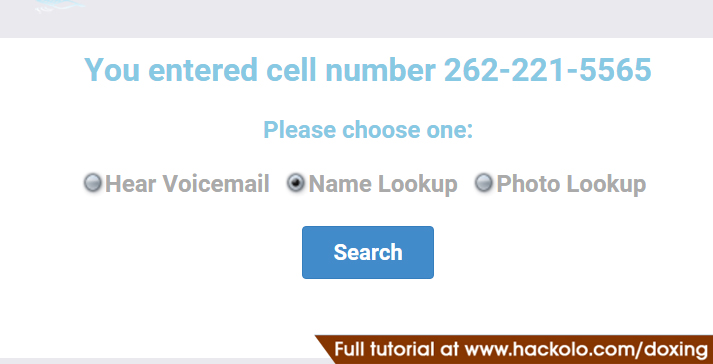
Talking about other services that can be used for doxing, reverse cell phone lookup usually ranks at the top. However, it requires the user to have your cell phone number to find your other private information such as name, email address, age, home’s address, and so on.
Furthermore, as the name suggests, it also works in a reverse way. If someone wants your cell phone number, they may probably be able to get it if they have some of your other private information.
There also seem to be many such services that can be used by someone looking to dox you.
-
Whois search

Whois is a website that shows most of the private information related to a website’s owner, including their name, phone number, email address, and so on. However, it can be used only if you have a website registered on your name.
This particular service also seems to be working well for many for doxing not only individuals, but also companies. After all, it’s pretty common for companies to have a website.
A simple whois search requires only putting in a domain name owned by you or your company, and the results may give away almost all your private information you shared with the domain registrar while registering the domain name.
The Reasons for Doxing Someone
As mentioned earlier, doxing may be done for various reasons. Sometimes, it may be done just out of curiosity, while some other times, evil intentions may be involved. Usually, doxing isn’t considered a cyber crime or anything of that matter if it doesn’t cause any harm to the one who has been doxed.
- Curiosity
- Harass, blackmail
- Stalk
However, many a times, when someone resorts to doxing simply because they want to harass, blackmail, or do anything harmful to someone, it’s surely considered a crime and punishable offense. So it actually comes down to the reasons behind doxing someone that decide whether it’s considered unethical or not.
However, unfortunately, over the past few years, doxing is seemingly being used on a widely scale to expose people and harass them. Hacking also seems to be a common reason many dox others for.
Hence, it doesn’t really seem to be a good thing at all, unless of course it’s being done by the law authorities or someone like that for finding out useful information about criminals or other such people. Other than that, there doesn’t really seem to be many reasons that justify doxing someone.
What Would Happen if you are Doxed?
To be very honest, regardless of the person’s intentions who doxes you, you end up being really vulnerable to social trouble and other similar major problems. After all, many a times, if you are doxed, even some of your most sensitive information, such as medical history, details about your personal life, your partner, friends, and family, may be accessed by someone.
Needless to mention, it obviously isn’t at all safe when such sensitive details are in the hands of someone you don’t even know personally. What’s worse that if such person decides to make all such information public, he may easily be able to do so without even revealing his identity. You can only imagine what trouble it may bring if such sensitive and private bits of information related to you and people related to you is made public.
In other terms: You can’t do anything about it! So protect yourself!
How to Avoid Doxing?
As hinted above, it makes sense to take steps to avoid getting doxed. So without further ado, we will simply take a look at some of the things you can do to avoid getting doxed.
Keeping the below given information private, and not sharing on the Internet, is definitely a good first step:
- Full name
- Email address
- Location
- Date of birth
- Details of your workplace
- Age
- Phone number
- Personal preferences and details about your relationship
We recommend that whenever possible, avoid sharing such private information. We know that sometimes it may be not be possible to avoid sharing such details, but it’s seen that most of the times, many end up sharing such details on the Internet for no good reason.
Anyway, if at all you have to share such details, you may consider following the below given steps to make sure that they aren’t easy to gain access to.
- If it’s a public or open place, such as a forum or something, don’t share your personal details openly. You may consider creating a new email address solely for sharing on such places.
- If you are sharing them on a social media website, you can consider changing the privacy settings. There are options that let you decide what information you would like to share with people you aren’t friends with, or even with your friends. If you want to ensure an even higher level of privacy, you may as well want to avoid your profile getting indexed on the search engines. Many social media websites allow making such changes.
- It’s also recommended to not share your private photos online, especially on platforms such as Picasa. Even if you want to, make sure the settings are strong enough to prevent strangers from gaining access to them.
- If you do several different things online and have accounts on different types of sites, it’s recommended to create a secondary email address only for such sites, or creating one each for such sites.
- You can find out if you are vulnerable to doxing by doing a simple Google search. If it shows results that reveal some of your private information, there’s an option to request the removal of such results.
- As far as preventing doxing through your website’s details is concerned, you can buy the “whois protection” service while buying your domain name. However, if you don’t want to pay anything extra, you can simply consider putting in wrong details, especially if you don’t want anyone to contact you using such details anyway.
- Make sure you don’t share your phone number with people you don’t know personally. This especially includes those you find on social networking sites. As mentioned above, your phone numbers can be used to find all your other private information using tools like “reverse cell phone lookup”.






The method has completely changed the way I do things, thank you.
Your method provides a clear roadmap to achieving success in X. I feel confident and empowered thanks to your guidance.
This method works! I’ve already seen improvements in my results after implementing your strategies. Thank you for sharing your knowledge and experience.
Your attention to detail is evident in the effectiveness of this method. Well done!
The method has completely changed the way I approach things, thank you.